How we protected 100% of our customers in less than a week
On October 16th, cyber security researchers publicly disclosed a vulnerability named KRACK in the WPA2 security protocol, which encrypts all traffic between modern WiFi access points and client devices. That same day, eero’s internal security and engineering teams rolled a fix out to our beta customers. A day later, we began rolling out the security patch to all customers. As of October 22nd, less than a week after the KRACK disclosure, 100% of eeros had been updated to protect against the security vulnerability. That’s faster than most companies even released a patch, let alone actually updated their products. In fact, all eero networks were updated before some companies even acknowledged the vulnerability at all.

And that’s because eero is designed to be not just nimble, but exceptionally reliable. To move fast, but break nothing. We’re laser focused on WiFi and have full control over the entire system — both the hardware and all the software. This allows us to react quickly to ensure our eero systems are always up-to-date. With more and more consumers depending on WiFi for everything they do in their homes — watching TV, streaming music, even turning on lights — reliable and secure WiFi is essential and should be expected.
Here’s the step-by-step of how we fixed the KRACK vulnerability.
- We broke it down: As soon as the KRACK vulnerability was announced, a dedicated team of eero engineers, security experts, and customer support leads worked quickly to understand how the issue affected eero customers and developed a solution for eero systems.
- We tested our fix: Once our engineers implemented a fix, it was rigorously tested with our own custom, in-house testing suite. From there we pushed it to employee and beta networks and leveraged our in-field diagnostics programs to ensure that all updated eero systems were performing as expected. This multi-staged and data-driven approach to product quality reduces risk, increases our ability to move quickly, and ensures that when we do send updates to customers, they’re exhaustively tested.
- We deployed it over the air: We shipped the fix to customers by sending over-the-air updates to all eero devices. Updates are sent automatically and in stages, to ensure we can adjust to feedback we get in the field in real time. That means no downloads, manual restarts, or customer service calls are required, unlike with many other WiFi systems. Our customers don’t have to be on high alert for issues like KRACK because we handle them automatically.
- We monitored feedback: Once we release software, we measure and gather customer feedback through our real-time diagnostic systems and all of our other customer feedback mechanisms. This ensures that if there are any other updates that need to happen, we can react quickly.
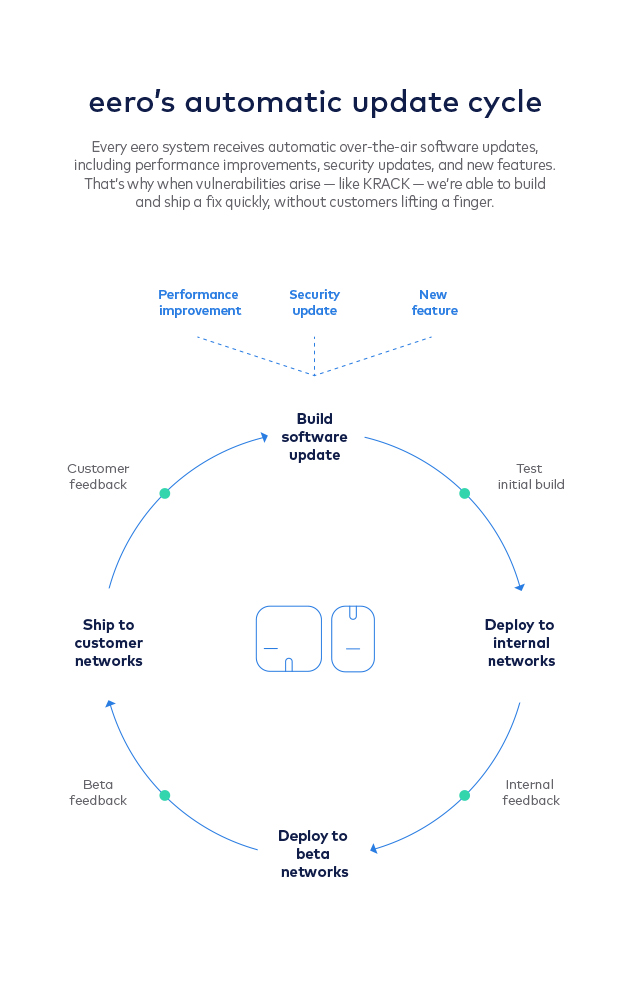
We use this process for all software updates: performance improvements, routine security updates, and even new features. This year alone we’ve sent millions of successful software updates to our customers with a greater than 99% acceptance rate. This model makes it possible to keep eero systems more resilient and more secure not just when massive vulnerabilities are announced, but every day. That’s why we were able to address the KRACK vulnerability so quickly — and it’s what we will do the next time a security vulnerability arises.
As our homes become more and more connected with smart speakers, televisions, light bulbs, and even basic appliances, the need for rapid and reliable software updates only becomes more important. Connected devices can make people’s lives easier and more convenient, but they also create more points of potential vulnerability. At eero we believe it’s important that security is never the tradeoff for this convenience. Customer safety should be built into the architecture of every product — not an afterthought. At eero, it is.
To learn more about eero and our built-in security please visit eero.com/technology. For more information on our premium security subscription services visit eero.com/plus.

You must be logged in to post a comment.