Coming in December, eero Plus members will be able to install the password management tool 1Password on their supported devices to easily create, manage, and secure their various passwords.
In 1835, Reverend Augustus Russell Pope filed a patent for the electric burglar alarm. It was fairly simple by today’s standards, but it was the first time that security was electrified.
It took another century before security entered a new realm – that of the digital. Despite the protests of the NSA (which sought to maintain a monopoly on encrypting data), German-American mathematician Horst Feistel created and published an encryption scheme known as ‘Lucifer;’ one of the first true digital ‘locks’ available to the public.
We’ve come along way since then, but the basic principle and concern behind these two inventions remains: how do you stop someone from taking your stuff?
Well these days, at least when it comes to computers and networks, the answer is usually a password. We’ve all got dozens of the things, and for the most part, we aren’t thinking about this.
Picking the right password
So let’s go through exactly what to think about when picking a password. And to do that, you have to understand what’s coming at you. A lock might stop someone trying to break down your door, but it isn’t going to do anything if that same person persuades you to give them a key.
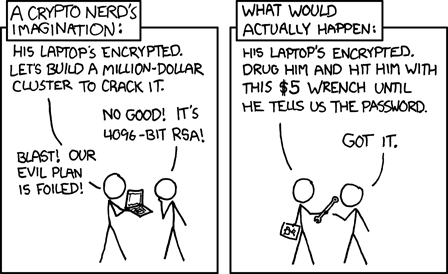
Broadly speaking, there are two primary ways that hackers crack passwords: brute-force attacks, and social engineering.
Brute-force attacks are fairly simple. Let’s say you have a four-digit numerical keypad lock. For each digit, there are ten possible inputs: the numbers 0-9. In total, that means there are 10,000 possible combinations, and only one will unlock the door. So if I want to get through that lock, and I don’t know the code, I’m going to have to sit there for hours, inputting different combinations before I finally get in. But eventually, the lock will open.
That’s a brute-force attack. Now the important thing to remember when it comes to computer passwords and brute-force attacks is that a computer program doesn’t really know what a word is. It also doesn’t really care about the difference between ‘a’ and ‘@,’ or between ‘s’ and ‘5.’ So all of the password requirements about special characters and numbers are completely meaningless when it comes to stopping a brute-force attack. All that really matters is password length.
To take the keypad lock above, for example, adding a single extra digit increases the number of possible combinations by a factor of 10 – 100,000 in all. Each letter, number, or symbol you add increases the amount of work a brute-force attacker has to do exponentially.
So long passwords are good. But what about the second kind of attack?
Social engineering is a catch-all term for any kind of infiltration targeted at the human element. Think of spies in movies who wear something flashy and persuade people to let them into places they shouldn’t. Or when those same spies dress up as exterminators or window cleaners to get into buildings.
The part of social engineering you need to worry about when choosing a password focuses on information. Because in the age of social media, someone who wants to steal your data can get a lot of personal information off of your Facebook page. Birthdates, pet names, anniversaries, it’s all out there, and it’s all pretty frequently used for passwords. So if someone’s trying to crack your password and they don’t have the time to brute-force it, then guessing things linked to personal information is a good way to go.
Doing that can also drastically reduce the time it takes to run a brute-force attack. If I know that your password is in some way connected to your anniversary, there are only so many different ways for you to type that in, and therefore only so many different permutations I need to type in before I can access your data.
Therefore, when you pick a password, avoid anything that’s easily connected to you. Or, at the very least, pick something that isn’t publicly available to anyone with an internet connection.
So to recap, your password needs to be long, and it needs to avoid personal information and if you receive an email asking for your password, no matter how authentic or official it looks, be suspicious. Even security-sensitive government officials fall for simple email phishing and it can have history changing consequences.
Remembering your password
First things first, do not write it down. You can have the best password in the universe, but it won’t mean a thing if it’s written on a sticky note next to your computer. So it has to be something you’ll remember. There are too many tricks to memorize words and phrases to list here, but one thing to keep in mind is that passwords with numbers and special characters are only marginally more secure against brute-force attacks than passwords with nothing but letters. Therefore, if you’re generating your passwords in your head, it’s more important to pick a long and memorable password than including letters, numbers, and special characters. Maybe it’s a quote, or a phrase from a book, but a set of words with more than 10 characters will put a stop to the easiest types of attack.
Anyone who can brute-force something longer than that is also probably somebody who has better ways of getting what they want. Famously, the CIA was once asked about how they crack passwords. And the answer was that they don’t – they crack people.
To further complicate matters, coming up with a sequence of letters and words that aren’t connected to your personal information but are easy to remember usually have their own problems. If you use a song lyric or a favorite quote, those are easy to remember because everybody knows them. If your password is part of the world’s shared culture, there’s a good chance they appear in password dictionaries used by hackers, so they’re still not great passwords.
The problems don’t stop there. Even when you come up with the mythical password that’s long, easy for you to remember, not connected to your personal information, and not something that might ever be guessed, there’s another way hackers will get around it. If you reuse your passwords across websites, then a hacker only needs to hack the weakest place you used that password in order to steal it and re-use it with your bank. Ideally, you’d use a unique, long, and hard to guess password everywhere, but you have hundreds of website logins – how are you going to come up with them all and remember them?
Fortunately, there are tools known as password managers that are designed to solve all of these problems. Using a password manager, you can generate long, completely random passwords that are unique for each site you use. When you visit the site in the future, you can copy and paste or automatically fill in the password to log in, and password storage is encrypted to protect against you losing your list of passwords – a much better solution than keeping things in a text file or a notebook. Many of these tools also offer features like notifying you if a website has leaked your password, or showing you all the sites you’re currently sharing passwords across. 1Password is a solid choice, and is included in a subscription for eero Plus members (coming in December).
If for some reason you can’t use a password manager, at least make sure you generate that long, hard to guess the password for each of the three to five most important websites you log into. It might not be the end of the world if someone hacks your account for a donut-of-the-month subscription, but it’s a much bigger deal for your financial and healthcare accounts.


You must be logged in to post a comment.