This is hardly news, but we all rely on the internet. A lot. And that’s true at a far deeper level than most of us are willing to admit.
When someone says ‘The Internet,’ most people think of websites. Or email. Maybe even Netflix or Facebook. These are all very clear examples of the internet in use; you type something into a keyboard, you click something with a mouse, you know the drill.
However, when you swipe your card at a grocery store, or when you buy a train ticket, you’re also using the internet. If you happen to own certain brands of thermostats or certain WiFi routers, you’re using the internet every time you turn on the lights in your house.
And there’s really no going back, barring literally life-changing efforts, and a very specific lifestyle. But that’s a topic for another time.
So we’ve established that we all rely on the internet. Therefore, it’s no surprise that we’re all pretty worried about cyber-attacks. And that’s pretty sensible. However, some of that fear stems from a lack of understanding – no surprise given the complexity of network and computer security.
There’s a few notable incidents, however, that can help us all to better understand the methods, the goals, and the realities of cyber-attacks.
Stuxnet (First Identified in 2010)
Stuxnet was a seminal attack for a multitude of reasons.

The central control room of nuclear power plant. Fragment of nuclear reactor control panel.
Stuxnet was a cyber-weapon targeting the nuclear centrifuges stored in the Natanz nuclear facility in Iran. These centrifuges spun at extraordinarily high speeds in order to alter uranium into a weapons-capable form. They also needed to spin at very precise rates; too fast or too slow and they could explode. Their speed was regulated and controlled by a computer.
Iran’s security experts were very aware of the potential for digital infiltration, and so they “air-gapped” these computers. An “air-gap” is when computers operate on their own, local network, frequently connected by physical wiring, rather than by wireless communication. The advantage of such a system is that it makes it difficult for an attack to get access to the network – you basically have to be on site.
However, Stuxnet found a way around that problem. By infecting the computers of scientists working at Natanz, Stuxnet was able to spread to USB drives that were eventually carried into the facility. When those USB drives were plugged into computers on-site, Stuxnet infected them as well, spreading to every machine on the closed network.
Operating in the background, Stuxnet then altered the speed at which the centrifuges spun, causing them to sheer from their bases and destroying nearby equipment in the process. Initially, these incidents seemed like random errors. In fact, it took years before Stuxnet was discovered.
To this day, there has been no official attribution of the attack, though the bulk of the evidence and the popular consensus points to a combined effort by the United States and Israel. Both countries deny their role.
So why are we talking about an attack likely carried out by one or more governments against another?
Well, Stuxnet brings up a couple of important points about the new age we live in:
- The connection between computers and physical infrastructure is undeniable, dangerous, and almost impossible to break. Power plants can be shut down, oil pipelines can explode, and dams can be burst, not by explosives, but by hostile computer programs.
- “Air-gaps” are not a perfect solution. With the right programming and the right targeting, hostile programs can “jump” those gaps and infect closed networks. The important part of this for your life is the understanding that you’re almost never as disconnected as you think or hope you might be.
- The human element is almost impossible to account for. Security measures might mandate that USB drives be left on-site, and that all work on a given project be conducted on a closed network, but people are people. One person getting lazy is sometimes all it takes.
Even if you’re not trying to create a nuclear weapon in an underground facility, these are still lessons you should take to heart.
Ukrainian Howitzers (Identified November 2016)

In 2016, Ukraine was at war with separatist elements; separatists sponsored, armed, and assisted by the Russian government. And their artillery battalions were being absolutely devastated. By the end of the year, almost 80% of their Howitzer artillery pieces had been destroyed.
The culprit? An Android app.
In an effort to improve the performance of their aging, Soviet-era artillery pieces, a member of the Ukrainian military wrote an Android app that calculated targeting information with extraordinary speed. However, Russian intelligence agencies seem to have caught on.
A piece of malicious code was attached to the app in an update, code that seems to have passed along location data to separatist forces. As a result, Ukraine’s artillery forces are almost completely destroyed.
Now, assuming you weren’t building a nuclear weapon, it seems fair to assume you also don’t have artillery units. But what you likely do have is a smartphone, and that smartphone likely has some form of GPS tracking. Here’s what’s relevant:
- Location data is not harmless. If you’re giving it up, make sure you know to whom, and for what purpose. And if someone gets a hold of it, don’t underestimate how much damage it can cause you.
- While it’s unlikely your phone is being used to aim a Howitzer, the devices it’s connected to and the updates it receives are still important to keep track of. Connecting to a compromised device can easily compromise your device in turn, and downloading updates from the wrong source can place your information (and maybe even your safety) in jeopardy.
WannaCry Ransomware (Identified May 2017)
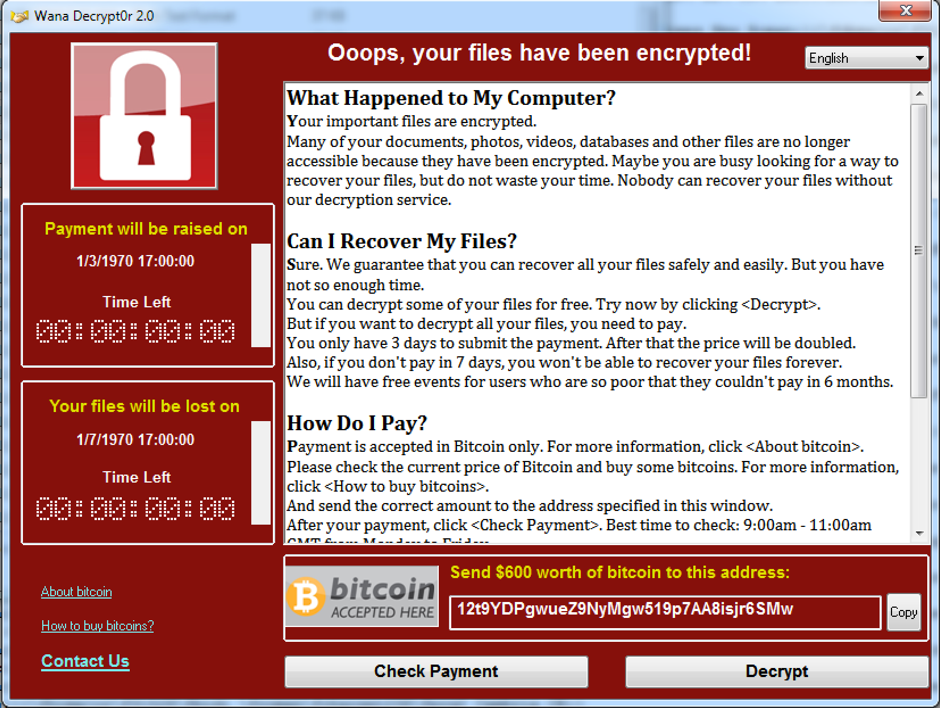
Moving away from nation-state level power plays and sabotage, let’s get to an incident that affects normal, everyday people who don’t run militaries or own nuclear weapons.
In May of this year, thousands of people turned on their computers only to be confronted by an open text file, a text file informing them that their computers had been completely encrypted. At the bottom were payment instructions, and a promise: pay the ransom, and you get your files back. Don’t pay… and the price goes up.
Payment was to be delivered in bitcoin (for those unfamiliar, bitcoin is a digital currency driven by complex cryptography. Long story short, it’s not tied into the normal banking system, so it’s much harder to trace if you’re being paid a ransom), routed through Tor, what’s known as a “packet anonymizer.” Tor basically bounces your internet traffic all over the world before it reaches it’s destination, making it difficult to track you down.
WannaCry showcased the ways in which a collection of technologies, working together, can make an illegal money-making endeavour much easier. Before technology, if you wanted a ransom for something, you had to physically take it first. Then you had to show up somewhere to actually get your money. Now things are a lot less physical, and it’s a lot easier to stay out of jail.
Takeaways:
- Tools like Bitcoin and Tor have made criminal enterprises far easier. Now you can extract payment from your victims largely without fear of capture, especially if you layer these kinds of techniques and technologies. Technology can be used for good or for ill, but once the potential exists for it to be misused, someone’s going to do it.
- Similarly, encryption, designed as a tool to protect information from prying eyes, can also be turned to malicious purposes, locking away user’s data behind an impenetrable wall.
It’s worth noting that the attacks listed here are on the outer edge of what’s possible. Two of the three were also likely executed by governments, against governments. However, they do demonstrate what’s possible. And once people know it’s possible to blow things up with a computer, it’s only a matter of time before someone tries.
Thus, we find ourselves in the midst of an arms race. Computer security companies and government agencies are constantly trying to patch holes and develop new defenses, while attackers are equally diligent in their search for exploits.
The most important thing for those of us on the sidelines to do is to maintain our awareness of our connectivity. Understand what angles you can be attacked from, and understand the targets attackers seek. Limit your vulnerabilities as much as you can, but be prepared for your defenses to fail. And have a plan for when they do.

You must be logged in to post a comment.