As more hotels offer free WiFi, business and leisure travelers alike have breathed a sigh of relief, knowing that, once they get to their destination, they can easily hop online in the lobby or from their room. There is at least the illusion of security, with network passwords provided on little slips of paper at check-in, or a system that demands your room number to gain access. So it’s safe, right?
Unfortunately, hotel WiFi networks — even ones that seem to diligently check your guest credentials before allowing you to connect — are not any safer than other public WiFi and should be treated with the same caution as any hotspot you might encounter at a coffee shop or airport. More alarmingly, recent reports have revealed that hotel WiFi networks are being targeted by hackers and data thieves, both because of how users let their guard down and because of the high-value information accessible on the laptops of people traveling for work.
As with other public WiFi, hackers use sniffers to capture sensitive information, set up honeypots or other network imposters to trick you into logging on, and use other means to install dangerous code onto your system.
Though the criminals attacking hotel networks use a variety of tactics, one recent method involved emailing hotel employees and tricking them into opening attachments that introduced malware to spy on guests, capture passwords, and monitor transmissions throughout each hotels network. Their spyware tracked every website visited by those who used the WiFi and had access to all information they sent and received using that connection, unless it was encrypted.
Investigators also reported uncovering in the summer of 2017 a ring of Russian hackers that had deployed an attack like this and used a powerful tool leaked from the NSA, called EternalBlue, to spy on guests through their hotel’s WiFi. These particular attacks are reported to be politically motivated and focused on capturing the information of business and government travelers, but they highlight the vulnerability of these internet access points on which so many of us have come to rely.
With the Russian scheme using Eternalblue, login credentials can be captured from connected devices, even if they aren’t typed in! This alarming advancement in high-tech thievery is, understandably, cause for concern.
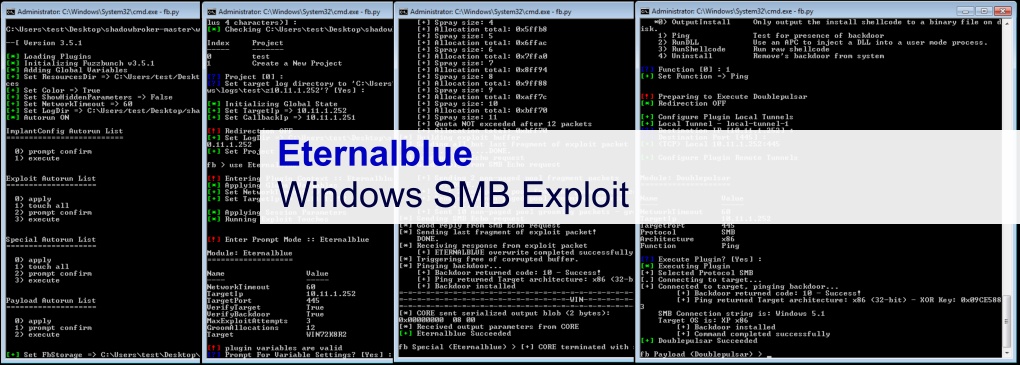 Image from: virtualhackinglabs.com
Image from: virtualhackinglabs.com
With these wide-ranging theft operations exposed, security consultants warned travelers in the U.S. and abroad of the threat and advised that publicly accessible WiFi networks should be avoided.
Pro Tip: If you’ve traveled and used hotel WiFi in the past year, take the precaution of changing the passwords for your online banking, using standard guidelines for making those accounts more secure, including two-factor authentication.
Some people took comfort that the Russian crime ring was targeting hotels in Europe, but on the heels of this revelation came a reminder of the general vulnerability of hotel networks. A recent report explained that a common wifi commonly used by hotel chains is particularly vulnerable to hackers. A security patch has been released for the device, but, as with other software updates, it is possible that a significant portion of hotels haven’t yet installed it.
It’s safe to assume that if you’re on hotel WiFi, you’re being snooped on by someone. And you can’t really know whether the spy who has access to the WiFi you’re on is seeking specific information, access to a corporate account, or targeting a high-value individual’s credentials. They could be a garden-variety snoop just looking to steal your bank account information or gather enough data to impersonate you.
How to protect yourself
Fortunately, there are steps you can take to protect yourself if you opt to use hotel WiFi. First, regardless of how secure they make it seem, treat hotel WiFi like any other potentially hazardous public WiFi. Being aware that these connections are not secure is your first step.
Beyond that, if you must use the WiFi at your hotel, you can protect yourself by using a Virtual Private Network (VPN). Even if the network you’re connecting to has been compromised by malware, sniffers, or some other tactic, if you use a VPN, all the attackers can see is encoded and encrypted versions of what you’re doing. They can’t intercept it, can’t read it, and can’t capture the private information you transmit.
As an alternative, rather than connecting to your hotel’s WiFi, you can use your cellular connection. Using your phone as a hotspot to connect your laptop or tablet to the internet is much more secure. Alternately, you can travel with and use a separate mobile hotspot that taps into a cellular signal.
And, while we’re talking about your security at the hotel, keep in mind that this same malware that’s infecting the hotel’s WiFi could have also been downloaded into their other systems. Prior to crooks focusing on stealing info from guests, there had been a long history of schemes for accessing hotel’s customer data. Opt to use credit cards instead of debit cards at hotels, as debit cards provide less protection for security breaches. Though you can’t fully protect your private information in their booking system, using a credit card can reduce your financial pain and hassle should hackers access the hotel’s payment records.


You must be logged in to post a comment.